[ad_1]
When Apple dropped macOS Sequoia final month, it added new selections like window snapping and the flexibleness to administration your iPhone out of your Mac. Along with surface-level modifications, nonetheless, the mannequin new substitute furthermore launched a protracted assortment of patches for safety vulnerabilities. On account of it occurs, one amongst these vulnerabilities was found by none aside from Microsoft, and is type of regarding for Macs used inside organizations.
How Safari’s TCC flaw works
Microsoft described its findings in a weblog submit on Oct. 17, virtually one month after the Sept. 16 launch of macOS Sequoia. The corporate calls the flaw “HM Surf,” named after the teachable change contained in the Pokémon assortment, which they found permits unhealthy actors to bypass Apple’s Transparency, Consent, and Administration platform for Safari. TCC usually ensures that apps with out applicable permission can’t entry corporations like your location, digicam, or microphone. It’s important for preserving your privateness from apps which is able to in each different case need to abuse it.
Nevertheless, Apple affords quite a lot of of its personal apps entitlements that permit them to bypass these TCC roadblocks. It is Apple’s app, in any case, so the corporate is acutely aware of it is not malicious. In Safari’s case, Microsoft discovered the app has entry to your Mac’s cope with e-book, digicam, and microphone, amongst utterly completely different corporations, with out having to bear TCC checks first.
All that talked about, you proceed to return throughout TCC checks whereas utilizing Safari all by net pages: That is what occurs once you load an web net web page, and a pop-up asks do you must’ll permit the scenario entry to at the least one issue like your digicam. These TCC settings per web site on-line are saved to a listing in your Mac underneath ~/Library/Safari.
That is the place the exploit is accessible in: Microsoft found you could possibly change this itemizing to a novel location, which removes the TCC protections. Then, you could possibly modify delicate recordsdata inside the exact dwelling itemizing, then change the itemizing as soon as extra, so Safari pulls from the modified recordsdata you set in place. Congratulations: You’re truly able to bypass TCC protections, and take an image with the Mac’s webcam, together with entry location data for the machine.
Microsoft says there are a variety of actions unhealthy actors might most definitely take from this occasion, together with saving the webcam image someplace they will entry it later; doc video out of your webcam; stream audio out of your microphone to an out of doors present; and run Safari in a small window, so you do not uncover its practice. Importantly, third-party browsers mustn’t affected correct proper right here, as they need to take care of Apple’s TCC necessities, and have not obtained Safari’s entitlements to bypass them.
Whereas Microsoft did uncover suspicious practice in its investigation which is able to degree out this vulnerability has been exploited, it couldn’t say for constructive.
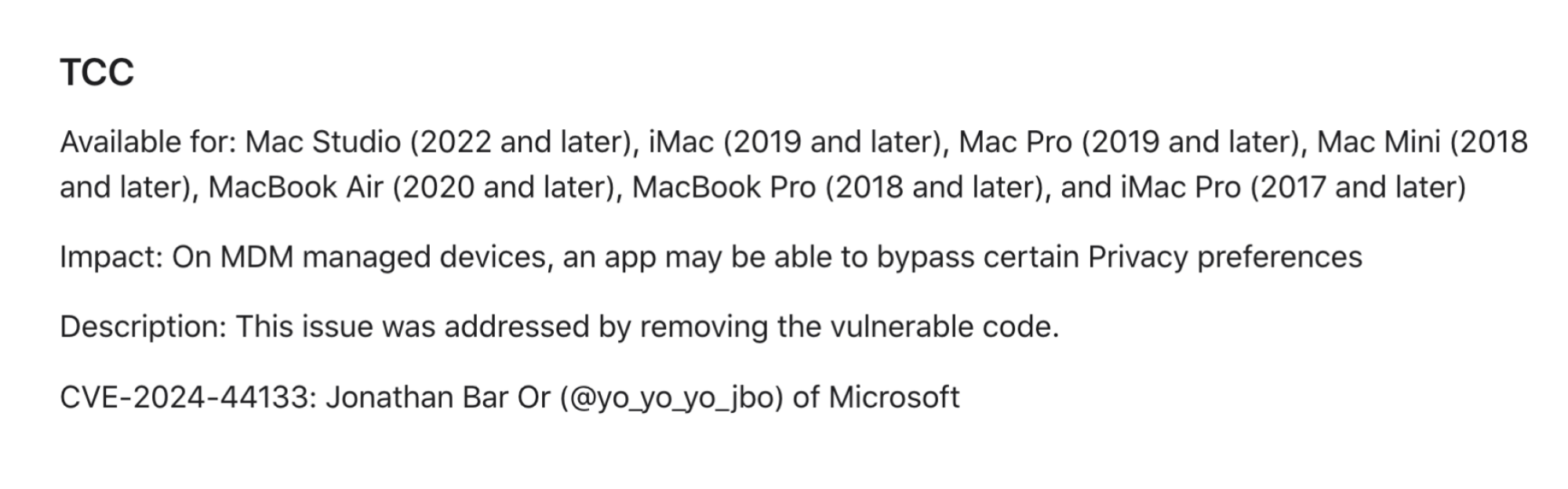
This vulnerability solely impacts MDM-managed Macs
After discovering out Microsoft’s report, ou could be apprehensive relating to the prospect of unhealthy actors snooping in your Mac by means of Safari. Nevertheless, what is not made categorical correct proper right here is that this vulnerability solely impacts MDM-managed Macs, i.e. Macs belonging to organizations managed by a central IT service. That choices Macs issued to you out of your job, or a pc belonging to your college.
Apple confirms as a lot in its safety notes for macOS Sequoia, in a relatively short-term entry contemplating the privateness and safety implications:
 Credit score rating score: Apple
Credit score rating score: AppleIn any case, the flaw continues to be essential, nonetheless it’s further restricted. You do not have to emphasize about Safari in your private Mac permitting hackers to entry your webcam, microphone, and web site. Nonetheless do you must do have a Mac issued from work or college that’s MDM-managed, that could be a precedence, and also you may need to organize the substitute as shortly as attainable.
Patching the flaw in your MDM-managed Mac
This flaw impacts the following Macs: Mac Studio (2022 and later), iMac (2019 and later), Mac Expert (2019 and later), Mac Mini (2018 and later), MacBook Air (2020 and later), MacBook Expert (2018 and later), and iMac Expert (2017 and later).
It is attainable your group has already issued the substitute in your Mac, whether or not it’s eligible. Nevertheless, in case your machine is not working macOS Sequoia, research alongside collectively along with your company or college’s IT to see when an substitute will flip into obtainable.
[ad_2]